~hackernoon | Bookmarks (2032)
-
Applying Modern Technology to Business: Shoyu Ro’s Path to Success
Shoyu Ro’s journey from an intern to a tech entrepreneur showcases his expertise in AI and...
-
Adversarial Settings and Random Noise Reveal Speech LLM Vulnerabilities
This section details the attack and countermeasure settings for SpeechVerse. Using a step size of 0.00001...
-
Datasets and Evaluation Define the Robustness of Speech Language Models
This section describes the datasets and evaluation methods for SpeechVerse. The training data includes 2.5K hours...
-
Adversarial Attacks Challenge the Integrity of Speech Language Models
This section details adversarial attacks and defenses for spoken QA in speech language models (SLMs). It...
-
The HackerNoon Newsletter: Space Telescopes Might Be Seeing More Than They Bargained For (2/6/2025)
How are you, hacker? 🪐 What’s happening in tech today, February 6, 2025? The HackerNoon Newsletter...
-
HackerNoon Decoded 2024: Celebrating Our Startups Community!
Welcome to HackerNoon Decoded—the ultimate recap of the Startups' stories, writers, and trends that defined 2024!...
-
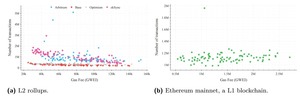
Why Gas Fees Drop as Transaction Volumes Increase on zkSync
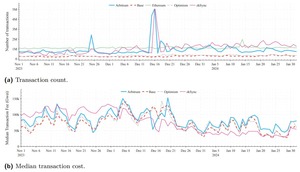
The analysis reveals that on L2 rollups like zkSync, gas fees tend to decrease as transaction...
-
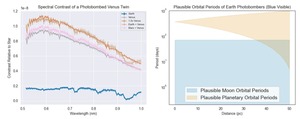
Mitigating the Effects of Photobombing in Exoplanet Observations
Photobombing from neighboring planets complicates exoplanet observations, but strategies like larger telescopes, improved detector sampling, multi-epoch...
-
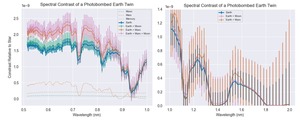
How Nearby Planets Impact the Spectra of Earth-like Exoplanets
Photobombing by neighboring planets, such as the Moon or Mars, introduces noise and flux variations in...
-
How Planets 'Photobomb' Earth's View in Space Telescope Observations
This study highlights how photobombing by neighboring planets, including the Moon, affects the observation of Earth-like...
-
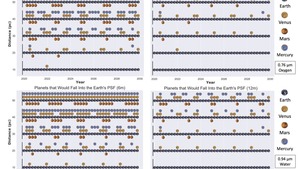
How Other Planets and Their Moons Sabotage Our Search for Earth Twins
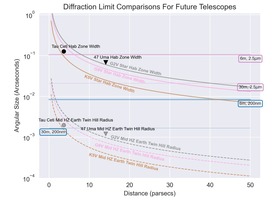
This study explores how the diffraction limit of 6m space telescopes can blur the images of...
-
Space Telescopes Might Be Seeing More Than They Bargained For
This study explores how diffraction limits of space telescopes can cause “photobombing” by nearby planets and...
-
Inscriptions Trading and Gas Fee Analysis of the zkSync Era
The trading of zkSync Era's zrc-20 sync and era-20 bgnt tokens shows differing activity levels, with...
-
Meet Exohood Labs, Avilo, and Luna AI: HackerNoon Startups of the Week
Welcome to HackerNoon Startups of the Week! Each week, the HackerNoon team showcases a list of...
-
Empirical Analysis of Inscriptions on Ethereum and EVM-Compatible Rollups
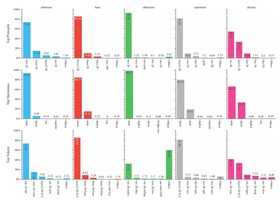
Our analysis reveals significant spikes in inscription transactions on Arbitrum and zkSync Era, with inscriptions dominating...
-
Why Multiplayer Skill Games Need a Domain-Driven Design
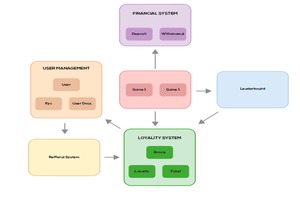
Domain-Driven Design (DDD) is crucial for skill game development, offering clear system boundaries, improved team communication,...
-
Meet Startups of The Year 2024 Nominee, SVEXA: Unlocking Human Potential with Precision Health & AI
SVEXA combines AI, physiology, and precision health to optimize human performance. Serving sports tech, military, and...
-
The HackerNoon Newsletter: Your Chatbot Isn’t Reading Words—It’s Counting Tokens (2/5/2025)
How are you, hacker? 🪐 What’s happening in tech today, February 5, 2025? The HackerNoon Newsletter...
-
Win Up to $2000 in the #blockchain Writing Contest by Aleph Cloud and HackerNoon
Join the #blockchain Writing Contest to win up to $2,000 by writing about decentralized AI, cloud...
-
How We Collected Data on Blockchain Inscriptions Across Multiple Platforms
The study gathers data from Ethereum and rollups like zkSync Era, Arbitrum, Optimism, and Base to...
-
HackerNoon Decoded 2024: Celebrating Our Society Community!
Welcome to HackerNoon Decoded—the ultimate recap of the Society stories, writers, and trends that defined 2024!...
-
DIY Enthusiast Hacks His Way Into Building His Own Musical Instrument (And It Rocks!)
I built a sci-fi bass from scratch, packed with a synth, a wireless transmitter, a hacked...
-
How Inscriptions Work on EVM Chains
This section explains inscriptions and ordinals, detailing key operations like deploy, mint, and transfer. It compares...
-
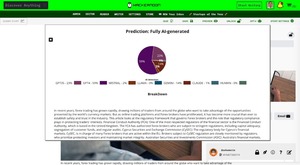
HackerNoon is Upgrading Its AI Detector 🕵️
HackerNoon is upgrading its AI detector from Originality.ai to Pangram. The tool came under HackerNoon’s radar...