~hackernoon | Bookmarks (2009)
-
How Scientists Are Teaching Soft Robots to Move Accurately
Controlling soft robots remains an open challenge, with both model-based (PCC, FEM) and data-driven (ML, Reinforcement...
-
Soft, Squeezable, and Smarter Than Ever: The Rise of Pneumatic Robots
This section reviews pneumatic actuation techniques in soft robotics, including bio-inspired designs, Pneunet actuators, and hybrid...
-
Meet PAUL: A Soft Robot That Moves with Air Pressure
This research presents PAUL, a modular soft robotic arm with pneumatic actuation, featuring 5 degrees of...
-
Naptha.AI Launches Its Decentralized, Multi-agent AI Platform
Naptha.AI launches its decentralized, multi-agent AI platform, enabling seamless collaboration across diverse environments. With open-source, scalable...
-
The Sandbox Introduces Major Enhancements For Creators And Brands To Build In The Metaverse
The Sandbox is the social gaming metaverse where people come together to create, connect, and play....
-
BYDFi Partners With Safeheron To Launch MoonX, The Ultimate Platform For Secure MemeCoin Trading
BYDFi, a well-known crypto exchange, officially announced the upcoming launch of its new Web3 on-chain trading...
-
Before AI Predicts Your Social Life, It Needs to Clean Its Data
In this post we'll continue working on link prediction with the Twitch dataset.
-
PINTU Reports 150% YoY Growth in Trading Volume, Driven by AI and Meme Token Surge
PINTU announced a 150% year-on-year (YoY) surge in trading volume, fueled by the explosive growth of...
-
TikTok Shopping Is Opening the Floodgates to Scams
TikTok Shop is generally safe to buy from, but it’s important to be careful when purchasing...
-
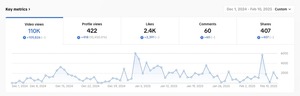
The TechBeat: Hackers Are Becoming a Rarer Breed (2/12/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
AI Meets Bitcoin: How Rootstock Powers the Future of Trustless AI
Rootstock is the best place to build AI-driven blockchain applications. It brings together Bitcoin’s security and...
-
Regulatory Clarity Will Define Crypto Wallets in 2025
Web3 wallets are at the core of the Web3 ecosystem. Top wallet providers like MetaMask found...
-
An Outline of the Dark Matter Thesis
To explain DM, we introduce a few simple WIMP models that can bypass present constraints and...
-
What Are the Most Popular Methods of Dark Matter Detection?
In this section, we describe the most popular methods to detect DM.
-
Some of the Most Popular Dark Matter Candidates: Looking Into the Standard Model
These are DM candidates, which were produced thermally in the early universe when it was in...
-
Vibe Coding - A New System of the World
Software engineer and software entrepreneur, Woody Hayday, says AI will soon do a better job than...
-
Security's Moving Parts 01: Linux Access Control Mechanisms
Nikolai Khechumov: Security's Moving Parts is a series of articles on security in software and hardware....
-
Social Recognition: A Must for Developers in Today's World
The role of a developer has changed as the world has changed. It's no longer enough...
-
The Myth of Connectivity: Uncovering the Global Blueprint of Digital Deception
This paper is presented as an analysis of transnational misinformation diffusion, showing that cultural, thematic, and...
-
fmt.Sprintf: Looks Simple But Will Burn A Hole in Your Pocket
This article explores various methods for string concatenation and conversion in Go. It demonstrates that for...
-
Graphing the Gossip: Unraveling Social Media Conspiracies
This paper is presented as an ERGM-based analysis of transnational factors shaping tie formation in Facebook...
-
To PR or Not to PR, That Is the Question
Many founders and C-levels confuse marketing and advertising with public relations. PR focuses on maintaining a...
-
Tariffs or No Tariffs, Smart Dealers Are Betting on Used Vehicles - And You Should Too
Dealers who wait for a final ruling on March 6 will already be behind. Smart operators...