~hackernoon | Bookmarks (1997)
-
Struggling With DolphinScheduler Setup? This FAQ Can Help
Struggling with #DolphinScheduler setup? Our latest FAQ covers environment configuration, service startup issues & common errors...
-
Geospatial Data Holds Immense Value for the Pacific Islands
The time has come for Pacific Islanders to recognize the treasure we hold in our digital...
-
Pangea Founder & CEO, Oliver Friedrichs, Answers 10 Questions for Every Startup Founder
Founded in 2021 by cybersecurity veterans, Pangea provides AI security guardrails that protect organizations from generative...
-
Deepfake Porn is Ruining Lives—Can Blockchain Help Stop It?
The article contains invaluable information on how blockchain technology can effectively wipe out the viral spread...
-
The TechBeat: How to Scale AI Infrastructure With Kubernetes and Docker (2/19/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
A Phenomenological Study of WIMP Models: A Summary of Everything We Discussed
We have considered a generic U(1)x model which provides an economical extension of SM to accommodate...
-
Two Ways That Dark Matter Interacts With the SM Particles
In this model, there are two ways for the DM to interact with the SM particles.
-
WebAssembly (WASM) - The Silent Infrastructure Revolution
WebAssembly(WASM) has the potential to change the cloud landscape. It can enable workload deployments at the...
-
My Story as a Mentor: How Learning and Teaching Impacted My Life
I founded ADPList, a platform on which I was able to mentor people around the world....
-
AI vs. ML : What's the Real Difference ?
Artificial Intelligence (AI) and Machine Learning (ML) are two different concepts. AI is the broad concept...
-
The Moment I Forgot It Was a Machine
Explore a unique perspective on how ChatGPT is more than a tool, and how it became...
-
The HackerNoon Newsletter: AI Knows Best—But Only If You Agree With It (2/18/2025)
How are you, hacker? 🪐 What’s happening in tech today, February 18, 2025? The HackerNoon Newsletter...
-
Write About Spacecoin's Mission to Decentralize the Internet and Win From 15,000 USDT
Participate in the Spacecoin Writing Contest and write about Spacecoin's mission to decentralize the internet for...
-
Valentine Special: Hot or Not? The Unbalanced Scale of Modern Dating
Men are more likely to shrug and say, “Bang, next question” while women stare at a...
-
How Software Quality Assurance (SQA) Turns Chaos Into Clean, Reliable Software
Software Quality Assurance (SQA) is more than just testing—it’s a proactive strategy for building reliable, bug-free...
-
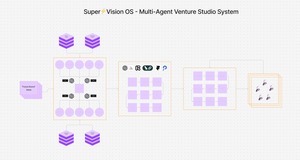
A Venture Studio Using Multi-Agent AI Systems to Make Better Investment Decisions
By far, the most compelling use case for Generative AI isn’t replacing human workers or automating...
-
The Art of Data Creation: Behind the Scenes of AI Training
Data Creation is the process of generating custom image and video datasets tailored to specific project...
-
How Journey is Bridging Revenue Dead Zones in B2B Sales
Traditional marketing methods that had worked previously are no longer delivering the desired results.
-
How S2|DATA's Libertas Tool Simplifies Restoration of Legacy NetBackup Data
Organizations worldwide have expressed concern about the long term viability of the NetBackup platform, after its...
-
Breaking the Chain: How Scribe Security is Redefining Software Supply Chain Protection
Software supply chain attacks are increasingly sophisticated and damaging, targeting the very foundations of digital infrastructure.
-
Hide and Seek in Memory: Outsmarting Sneaky Malware with Data Magic
The paper focuses on machine learning methods being applied to detect obfuscated malware in memory dumps...
-
The TechBeat: Cybercrooks Are Using Fake Job Listings to Steal Crypto (2/18/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
How to set up NetSuite Token-based Authentication (TBA) in Laravel
NetSuite offers various methods for authenticating and integrating with its system. Among these are: Token-based Authentication...
-
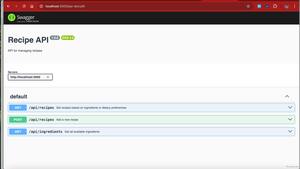
Making Cooking a Breeze By Building Your Own Recipe Finder With Nodejs
The Recipe Finder API is a versatile solution for efficiently storing and retrieving recipes based on...