~hackernoon | Bookmarks (1932)
-
My Wild Ride from Old-School Recruiting to AI-Smarter Outreach
Old-school recruiting sucked. AI’s my new bestie—cuts the grunt work, lands better replies. Check my journey...
-
Open Source Is Supposed to Be a Meritocracy—So Why Are Companies Trying to Buy Their Way In?
A recent survey by the Linux Foundation found that organizations contribute 7.7B USD annually to open...
-
Intelligence Isn't What You Think It Is
Intelligence is not about remembering facts or doing well on tests. It’s about living a life...
-
This Simple Python Script Will Finally Fix Your Messy Downloads Folder
Python developer Eric Mahasi created a tool that organizes your Windows Downloads folder. I added support...
-
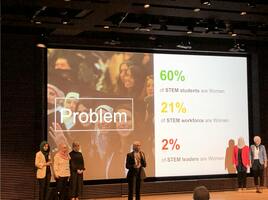
TechWomen Fellows Fight to Save U.S.-Backed STEM Exchange Program
On March 14th, 2025, thousands of women in tech received a devastating email. An international exchange...
-
The Internet’s New Privacy Tax: ‘Consent or Pay’
“Consent or Pay” is a relatively new approach that technology companies are using to comply with...
-
The Real Battle in Tech: Women Fighting Power, Not Men
The fight for gender equality isn’t just about cultural shifts or policy changes, it’s about power....
-
The Internet Is Full of Duplicate Requests—Here’s How Smart Developers Prevent Them
Idempotency is an essential tool for preventing duplicate operations, improving API stability, and ensuring consistent behavior...
-
AI Tries (and Fumbles) at Inflation Forecasting
Researchers evaluated ChatGPT’s ability to predict inflation from Sept 2021–Aug 2022. While direct prompts failed, narrative...
-
Can AI Predict Inflation? Testing ChatGPT on Macroeconomic Forecasting
Researchers examined ChatGPT-4’s ability to predict monthly macroeconomic trends (Oct 2021 – Sept 2022) using direct...
-
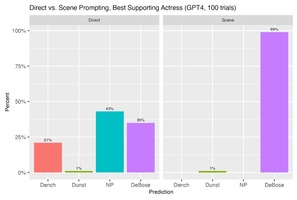
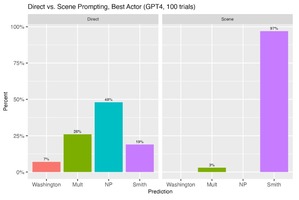
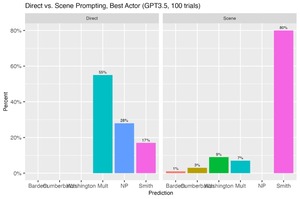
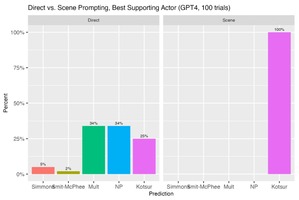
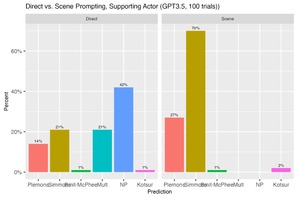
We Asked ChatGPT To Predict Oscar Winners—the Results Were…Interesting
Researchers tested ChatGPT’s ability to predict 2022 Oscar winners using two prompting methods: direct and future...
-
Why AI Answers Change Depending on How You Ask the Question
Researchers tested GPT-4’s forecasting abilities by comparing direct prompts with narrative-based storytelling. Findings suggest AI may...
-
Doctor, Doctor! AI Won’t Diagnose—Unless It’s in a Play
GPT-4 refuses to provide medical diagnoses directly but will generate medical advice through narrative storytelling. This...
-
Can ChatGPT Predict the Future?
This study tests ChatGPT-3.5 and ChatGPT-4’s forecasting ability by comparing direct prediction prompts to storytelling-based prompts....
-
The TechBeat: One Month Left to Win Your Share of 15,000 USDT in Round 1 of the Spacecoin Writing Contest (3/18/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
From Rome to the Riviera: Embracing Italy’s eSIM Revolution for Seamless Journeys
Italy’s eSIM revolution is reshaping travel, allowing tourists to stay seamlessly connected without physical SIM cards....
-
Dave: Not the Hero We Want, But the Hero We Need
Discover Dave, Cartesi's revolutionary fraud-proof system for Optimistic Rollups. Learn how this permissionless, Sybil-resistant solution secures...
-
Social Discovery Group Officially Named a Great Place to Work in Japan in 2025!
Social Discovery Group has been officially Certified by Great Place To Work in Japan. The recognition...
-
Overusing Implicit Returns Makes Your Code Harder to Read and Debug
Overusing implicit returns makes your code harder to read and debug.
-
The 5 Essential Skills Every Leader Should Have (And How to Build Them)
These five skills are crucial for leadership effectiveness. Without them, those in positions of leadership hold...
-
Want to Be More Productive? Pretend You Die Every Night
The concept is simple: When you go to sleep each night, your previous life is over....
-
Monographs and Their Role in Universal Graph Representation
Monographs generalize graphs by treating nodes as edges and simplifying morphisms. They offer a universal approach...
-
Will Musk Colonize Mars In His Lifetime? The Answer Won't Surprise You
Will Elon Musk colonize Mars in his lifetime? No, not in the grandiose Kim Stanley Robinson...
-
DeFi Yields Are a Lie—Here’s What You’re Really Earning
DeFi success comes from mastering risk management, not chasing high returns.