~hackernoon | Bookmarks (2012)
-
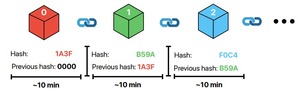
How Miners Select and Order Transactions in Bitcoin
This chapter defines blockchains and smart contracts, then explains that Bitcoin Core’s GetBlockTemplate creates three unwritten...
-
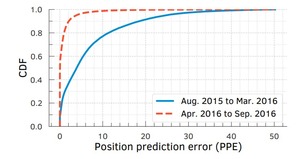
How Miners and Token Holders Impact Blockchain Fairness
This thesis introduces new metrics (SPPE/PPE) to audit miner fee norms, uncovers private‑relay “dark‑fees” and mining...
-
Not All Blockchain Transactions Are Created Equal
This thesis audits how miners prioritize transactions on Bitcoin and Ethereum, and analyzes token‑vote distribution in...
-
Google (gmail.com) Must Crack Down on SEO Spam Emails From Lead Gen Farms In India
Despite Google's near-omniscient algorithms and AI prowess, my Gmail inbox still looks like a dumping ground...
-
How To Create A Strong Web3 Brand
Simple template to create a strong Web3 brand like Ethena and Berachain.
-
AI’s Dirty Secret: The Energy Cost of Training the Next GPT-5
GPT-5 could be 5 to 25 times larger than GPT-4. Training LLMs is like trying to...
-
How Can Elon Musk Save Your Crypto?
Elon Musk can ignite meme coin hype, but only real engagement-like gamified quests-keeps crypto projects thriving...
-
The TechBeat: New Formula Could Make AI Agents Actually Useful in the Real World (5/6/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
Meet WISE MARKET, Winner of Startups of The Year 2024 in Delaware City/Supply Chain Tech (SaaS AI)
Wise Market is building AI-powered, B2B supply chain infrastructure that simplifies procurement, connects SMEs with manufacturers,...
-
An Update on Rust's March Project Goals: What's the Progress So Far?
This post provides selected updates on the progress towards these goals (or, in some cases, lack...
-
Spotlighting Tech's Rising Star: Dealita, Winner of Startups of The Year 2024 in Riga, Latvia
The Latvian startup Dealita.ai uses artificial intelligence to automate one of the most time-consuming stages of the investment...
-
VC Funding is Shifting from Gen-AI Apps to Deep Infrastructure
The past two years were dominated by “ChatGPT-for-X’ pitches and billion-dollar application rounds. Investors began to...
-
Meet Kuwait Mart, Winner of Startups of the Year 2024 in Kuwait City
Kuwait Mart is a homegrown e-commerce platform built to serve customers across Kuwait with speed, trust,...
-
Tracy Jin, MEXC: Why Universities Are the Backbone of Web3’s Future
MEXC Ventures’ IgniteX initiative supports Web3 talent worldwide — with a special focus on universities, early-stage...
-
Boost Team Wellness With UzairaAdvisory and Save 10% on All Our Business, Marketing & Tech Services
Book Your Preventive Healthcare Seminar with UzairaAdvisory—Boost Team Wellness and Enjoy 10% OFF Our Cutting-edge &...
-
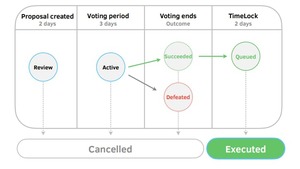
Behind the dApp: Understanding Blockchain Architecture
This guide covers blockchain basics, the crucial role of different node types (light, full, archive), and...
-
The TechBeat: Celebrating Vitruvian Man Day at SDG: A Tribute to Arts, Science, & Human Potential (5/5/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
How to Set Up a Free Oracle Cloud VM for Web Development (2025 Guide)
Oracle Cloud offers a free VM with 4 vCPUs, 24GB RAM, and 200GB storage (as of...
-
Spam vs Phishing: Know the Difference
While they may seem similar at first glance, there’s a big difference between spam and phishing,...
-
Ukraine is a Building a Drone Wall Against Russia
Russia’s fresh spring offensive against Ukraine “has already begun,” Commander-in-Chief Oleksandr Syrskyi said. The Kremlin is...
-
Six Side Characters That Stole The Show In TV Shows
Some TV shows have had side characters who have become big hits. The Vampire Diaries, Game...
-
A Beginner's Guide to Reading and Writing Smart Contracts on Explorers
Don't wait for dApp interfaces! Learn how to use blockchain explorers like Etherscan/Abscan to directly read...
-
From Zero to DR41: How I’m Ranking My New Site (and Aiming for “Socks” at 425K)
A new site I launched recently is ranked #1 on Google. I started from scratch and...
-
READ THIS: The Complete Guide to Based and Native Rollups
Based Rollups use Ethereum (L1) for transaction sequencing, while Native Rollups use L1 for execution verification,...